The Hybrid Cloud: A Flexible Approach
In an era where agility meets innovation, the **hybrid cloud** emerges as a hero in the world of IT infrastructure. With a blend of on-premise and cloud resources, it offers companies the flexibility to scale operations effectively. Think of it as having your cake and eating it too—more control over data with the sky-high benefits of cloud computing!
- **Increased scalability**: Businesses can scale resources up or down depending on demand.
- **Cost efficiency**: Pay for only what you use, making it more budget-friendly.
- **Improved security**: Sensitive data can be stored on-premise while non-critical workloads are handled in the cloud.
It's like a magician pulling a rabbit out of a hat—only this rabbit is made of ones and zeros that can float around the internet.
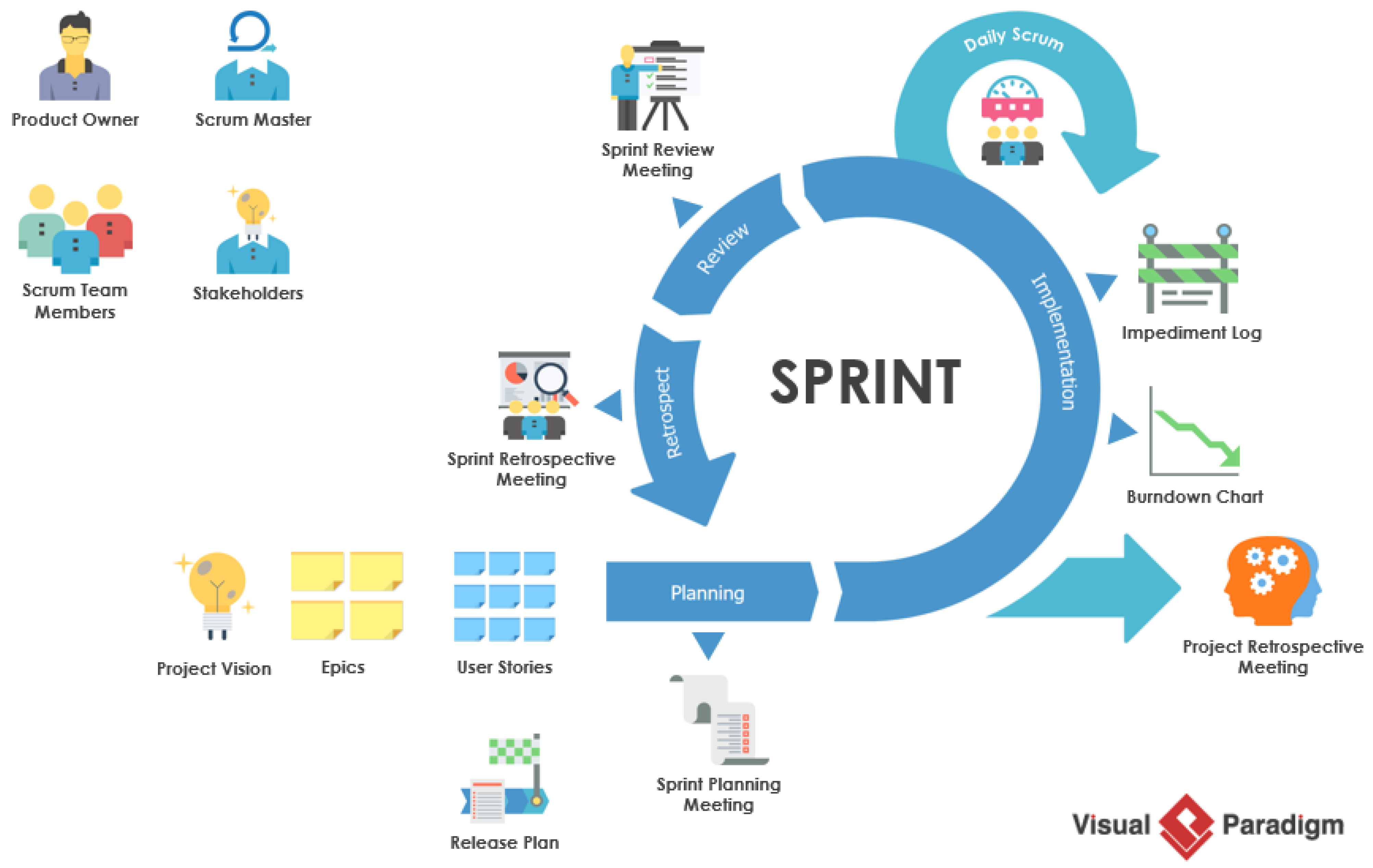
Scrum: The Agile Architect
Ah, **Scrum**—the agile methodology that helps teams navigate the chaotic waters of software development! Utilizing short sprints and regular check-ins, Scrum focuses on delivering value quickly and iteratively. It’s like having a GPS for your project: you know where you’re going, and your team can recalibrate if you hit a pothole (or a bug!).
Some key benefits include:
- **Faster delivery**: Accelerates the development process through iterative cycles.
- **Improved collaboration**: Fosters communication among team members.
- **Increased flexibility**: Allows teams to adjust priorities as needed.
It's the agile dance that keeps everyone on their toes, ensuring a seamless flow of creativity and functionality.
Ensuring Quality with Quality Assurance
In the realm of software, ensuring quality is akin to checking for wrinkles in your new suit before a big meeting. **Quality Assurance (QA)** ensures that each piece of software functions as intended, which saves companies from backtracking due to faulty releases.
QA is not just about testing; it's about **creating a culture of quality** that permeates through each stage of development. After all, wouldn’t you prefer a beautiful tapestry rather than a patchwork quilt?
Key strategies include:
- **Continuous testing**: Integrating testing throughout the development lifecycle.
- **Automation**: Using tools to run repetitive tests, freeing up human testers for more complex tasks.
- **User feedback**: Utilizing customer insights to enhance product offerings.
It's an ongoing process that emphasizes attention to detail, turning potential disasters into successful launches.
The Rise of Serverless Computing
Enter the age of **serverless computing**, where developers can focus solely on their code and leave the infrastructure to cloud providers. It’s like ordering takeout on a busy night—no need to cook, just indulge!
Benefits of serverless architectures include:
- **Reduced infrastructure management**: Developers can concentrate on building applications rather than managing servers.
- **Cost savings**: Handpicking resources means paying only for what you use.
- **Scalability**: Effortlessly scales up and down based on application demand.
With serverless computing, scalability is as easy as flipping a switch—just remember to turn off the lights when you're done!
Unlocking Insights with Analytics
**Analytics** is akin to a treasure map that leads businesses to valuable insights hidden beneath layers of data. Utilizing analytics can transform raw data into a narrative that shapes strategic decision-making, guiding companies through the jungle of competitors.
Here are some insights into effective analytics implementation:
- **Data visualization**: Transforming numbers into digestible graphics for clarity.
- **Predictive analytics**: Using historical data to predict future trends and behaviors.
- **Real-time analysis**: Making decisions based on current data, leading to agility in responses.
It’s like having a crystal ball that doesn’t require a secret incantation!
The Need for Ethical Hacking
**Ethical hacking** is the digital knight in shining armor, walking the tightrope between cyber protection and vulnerability exploitation. By preemptively identifying potential weaknesses within systems, ethical hackers safeguard organizations from malicious breaches.
Key components include:
- **Risk assessment**: Identifying threats before they can be exploited.
- **Penetration testing**: Simulating attacks to evaluate security measures.
- **Compliance**: Ensuring systems adhere to required regulations and standards.
Ethical hackers are the unsung heroes of cybersecurity, turning the tables on those with ill intent.
Embracing Full Stack Development
**Full stack development** is like being a culinary chef who can whip up everything from appetizers to desserts. They have the skills to develop both front-end (what users see) and back-end (the server, database, and application logic) components, making them invaluable team members.
Advantages include:
- **Versatility**: Skilled across multiple technologies, facilitating smoother collaboration.
- **Faster turnaround**: Speeding up development cycles with a comprehensive understanding of the entire stack.
- **Better communication**: Bridging gaps between developers and designers, enhancing project harmony.
Full stack developers are like Swiss Army knives in the tech world—multi-functional and ready for anything!
Data Warehousing: The Central Repository
**Data warehousing** acts as the central repository, gathering data from multiple sources and organizing it for analysis. Think of it as a well-stocked pantry, where each ingredient is carefully labeled for easy access when it's time t...